Five Steps to Cybersecurity
Improving your business cybersecurity posture can be difficult to wrap your head around. There are many people trying to sell you tools to make you secure but many won’t help do much, other than lower your bank balance. We’ve put together a starter list of things that you should think about to plan to protect your information and systems.
These five items can be considered an action list to get you started in understanding the cybersecurity risk to your business. It’s not unlike other areas of risk, but we’ll be more specific in where the risks come from, what’s potentially impacted and how to bring them back to within your appetite for accepting them.
1. Know What You Have
If you don’t know what you have, you won’t be able to protect it. If there’s an easily hacked bug in a common piece of software, does it apply to your business or not? You can’t respond and fix the problem if you don’t know it’s there to begin with.
- Make a list of all the important software you have installed on all your computers and servers. You can probably have a look at your invoices to reconsile what’s been paid. What’s the most common business software your team uses?
- Add all the online software-as-a-service (SaaS) software that you use. Things like Xero, Microsoft Office 365, Google Workspace, etc.
- Where do you store all your information? On laptops and desktops and servers or perhaps Onedrive, ShareFile, Dropbox, etc. Without all your data being available, that software installed on your laptop won’t help much.
- While you’re making the list, perhaps think about where all these IT assets are located. Who manages those sites?
2. Know Your Threats
With your list of all the software and services your business uses, you can start to think about what might go wrong and what’s the most likely event to cause you problems. Think about these risk in terms of likelihood and consequence.
- Insider actions by your own staff, either accidentally or on purpose are often the most likely threat. How good are your processes for ensuring everyone knows and does the right thing when dealing with your business information?
- Do you operate your own public website or email server that is accessible to the whole online world? Internet connected systems are being continuously scanned 24/7 and it’s an automated process that often doesn’t care if your website holds no sensitive information - it may be hacked anyway.
- How much do you trust your vendors that operate any IT systems for you or store your data? What if they had some of these problems, or if they went bankrupt?
- What is the consequence to your business operations or customer trust? Would you stop work for an hour or a week, would your customers still trust you, do you have regulatory or legal requirements to meet?
3. Document the Gaps
Your list of threats might be a bit depressing, but it’s the same situation for almost everyone in the modern digital world. On the positive side, now you know a bit more about the risks and you can plan to do something about reducing them as much as is realistic.
The gaps are where you know you have a risk but no people, process or technology to reduce that risk to within your appetite. What you’re actually doing here is a risk assessment and we can use that to help determine those next steps.
To really improve your cybersecurity maturity is tough. When thinking about these gaps also consider how they were caused to appear too. Lack of people skill, wrong tool for the job, perhaps a lack of process and oversight?
4. Make a Plan
Putting together a plan will need some additional expertise in order to prioritise the work against those gaps. What’s achievable and when depends on the urgency of the risks - how likely are they to happen and if they did happen, how bad would it be? You can use a risk matrix like that below to get a rating for each item you have. Each of those items is probably a “something” from step 1 above, which has a threat to it from step 2.
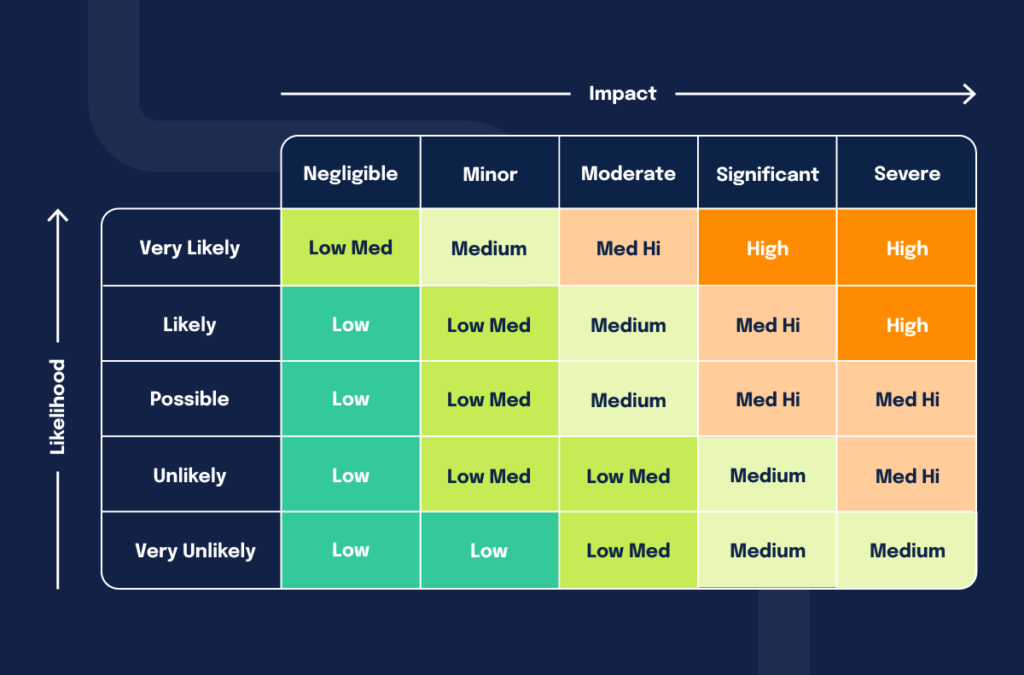
The typical priority is to deal with the highest rated risks first. If these were to occur then it’s going to be very bad for the business.
It’s also common that you can’t easily make these risks disappear entirely. Instead you should work on reducing the likelihood of the risk occuring in the first place. An example might be to introduce a two person process for sign off to reduce the likelihood of fraud or theft. Or to replace an old and unsupported system with a new version that does include support.
Think about the ingredients to your plan - who do you need, what amount of effort will it take, what new tools might be involved, etc. It’s a bit of project management 101, but like many things it’s ensuring the basics get done properly.
Don’t try and do everything at once. Many of those processes and IT systems are likely intertwined, so you need a clear view of what they each affect.
5. Execute the Plan
When you have a plan to address your first cybersecurity risk it’s time to make it happen. But you also need to know how to confirm it has been properly resolved. What testing or checks can be put in place now to confidently close the risk?
To confirm a technology risk is resolved, you might have people that can do testing for you and document the result. For highly technical aspects, you might need to engage an external penetration testing specialist to close it out.
After the work is done, you should reassess the risk to ensure the risk has been reduced enough to accept. It may be a case of doing enough for now and moving onto another risk with the expectation to come back and address it later, or after a dependency is resolved.
Finally, make sure that appropriate documentation is included in the work. Having one person carry out the changes for a technical fix might be quick, but if they’re not writing it down for the next person, the problem could appear again in the future.
Bonus: Keep Doing It
Once you’ve been able to do those five things unfortunately the work isn’t over, but you have come a long way. Things always change, so you need to regularly review systems, information and vendors as they come and go. If old things hang around too long and new things get the “quick and dirty” treatment, they will add risk.
The best way to stay on top of it is to make it part of your annual business planning and get it ingrained in your team’s culture. Unfortunately, that might also be one of the hardest!